TryHackMe: Easy Peasy Write-up
 |
| Easy Peasy CTF |
Introduction
In this article, I show you how to complete an Easy Peasy CTF room on TryHackMe. The room requires us to use nmap and gobuster to gain initial access and then use a weak cronjob to escalate to root. Now let's get hacking!
Enumeration
Nmap
Head over to port 80 HTTP and we get a default nginx web server.
Gobuster
I have scanned the site using Gobuster to find hidden subdirectories.
A rather interesting sub-directory /hidden, Traverse to the sub directory an we are welcomed with a shady looking room.
On further enumeration of the sub-directory we get another sub-sub directory /whatever
Heading there, we get a picture, not much info really.
On checking the source code we find something rather interesting.
I decoded it quickly inside my terminal and there’s the first flag.
I pretty much exhausted that port now I headed to port 65524 and I landed on the default Apache page, there we get a flag hidden in plain sight.
When we examine the source code, we get the code encrypted in the base.
I got some help decoding it on dcode.fr and I got a sub-directory
we find a path but before check it let’s check a dirsearch resalts
Something interesting on /robots.txt a hash
Let’s head over to TunnelsUp an online tool that aids in quick hash analysis
There’s an online tool Md5Hashing.net use it do decode the hash. There’s the second flag.
Now lets head on to the sub directory we found earlier and boom, we are in the matrix, or are we? First I got another hash hidden in plain sight.
Quick analysis on TunnelsUp and I realize it’s a sha2–256 hash.
Download the given wordlist easypeasy.txt and use it to crack the hash.
I used the tool stegseek to crack the image using the wordlist given
I got the password and it’s extracted to binarycodepixabay.jpg.out. Now lets view the content.
It’s a username and a password in binary form. I head over to cyberchef to decode the binary code and get the password.
Getting a shell
Now that we have a username and a password let’s login in. Remember the ssh port 6498 we found earlier, we have to specify that in since its not the default ssh port 22.
Let’s get those flags.
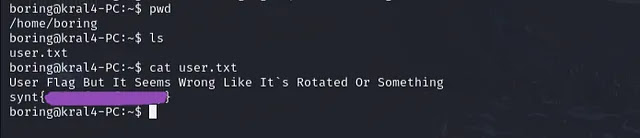
On the home directory we get the user flag but it looks kind of weird and there’s a note, and the flag is rotated.
I used an online tool called rot13 to rotate the flag and get the actual flag.
Privilege Escalation
Now we need to escalate privileges to get the root flag. I did some looking around and got a hidden file in /var/www/ directory. A bash script
The bash script can be edited to get a reverse shell onto our attacking machine. I Headed to pentestmonkey and got a bash script that I modified my Machine IP.
I edited the script and saved it, let’s wait for it to run.
Rememeber to setup a listener to catch an incoming connections.
Now let’s search for the root flag.
The flag was a bit hidden but I found it in the /root/ directory
Keep on learning and keep on hacking :)