TryHackMe - Library CTF [Writeup]
 |
| Library CTF |
Reconnaissance
Nmap
Let’s start with a nmap scan.
Nmap seems to detect two open ports, port 22 (SSH) and port 80 (HTTP). I think we should leave port 22 for a while since we have no idea how to brute force the port. Let's check the HTTP port.
How about directory-attack?
Gobuster
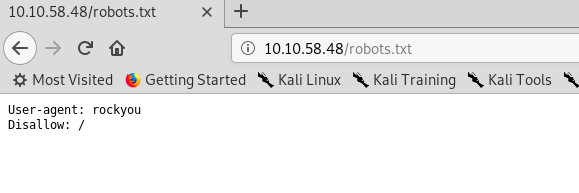
gobuster didn't return any interesting evidence except robots.txt. I think we should check that out.
User agent rockyou? I think the word list rockyou.txt is a hint to the challenge. What else can we extract from the page?
We’ve got a username called “meliodas” as the author of the blog post. Now, we have the username rockyou.txt as a hint and an unused SSH port. What’s on your mind now? It’s time to brute force with hydra.
Hydra
We are on the right track. Login to the ssh shell by using the following command and ‘iloveyou1’ as the login password.
User flag
Now we are inside meliodas' SSH shell. Let's grab the user flag.
The user flag is now with us.
Privilege Escalation
It is time to root the machine!. First and foremost let see which sudo command can be performed by the user.
The user only can use sudo python on bak.py file.
Root flag
I guess we can't do anything with the script because it is write protected. Since we only get sudo privileges when executing bak.py using Python. How about deleting the current bak.py and creating a new file that will allow us to create a root shell? Crazy right? Let's try that.
We can now capture the root flag.
Congratulation, you are now rooted in the machine.